[vc_row][vc_column][blog_single_full_content]Have you heard of data getting hacked from a mobile app and records getting stolen?
Data is the most vulnerable target for hackers breaking into servers via mobile apps. Mobile applications that businesses utilize to provide services to their customers or users are ordinary attack platform for hackers. Breach of mobile security gives hackers access to personal information. Like location, banking details, social networking, and more.
For instance, hackers can enter into a user’s device via an app. Once in the system, it can read data. Like personal messages, contacts, access device location, permit push notifications. And also determine the IP address of the mobile connection, along with admission to personal files on the device.
Hackers can gain debit or credit card numbers for any bank transactions. That is, with or without a one-time password. As they have the entire control of the mobile device in their manipulative hands. Hence in today’s world best mobile phone security of apps has become very important.
‘’One single vulnerability is all an attacker needs’’ – Window Snyder
A huge example of a mobile app security violation is the WhatsApp case. WhatsApp is one of the most popular apps used around the world, with over two billion users. Even with the end-to-end encryption control it offers, which guarantees better security, it contained a flaw. One of its functions lets the hackers inject malware into the user’s device only by calling on their phone. Post this incident, the famous Facebook bought WhatsApp and fixed this system flaw.
According to statistics, mobile applications are a crucial target for hacking, exploitation, and security breaches. In 2018 researchers found many types of weaknesses in mobile applications. As per their report, 46% of mobile applications have manipulation exposure.
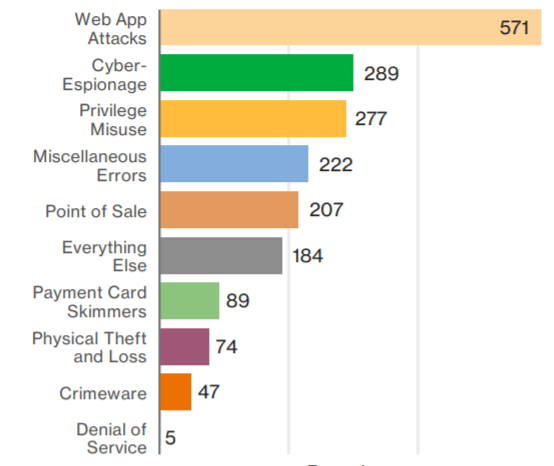 Their survey determined three out of five applications to have configuration errors, standard passwords, information leaks. And much more possibility of potential hacking. To avoid such risks and maintain a secure mobile app, developers need to change their structure. And lean more towards securing their users’ apps.
Their survey determined three out of five applications to have configuration errors, standard passwords, information leaks. And much more possibility of potential hacking. To avoid such risks and maintain a secure mobile app, developers need to change their structure. And lean more towards securing their users’ apps.
Importance of Mobile App Security
In today’s time, a mobile is a necessity, unlike in earlier times, when it was a luxury. Now, people seem incapacitated without a mobile. People use mobile for everything. For directions, payments, shopping, socializing, keeping fit, and more. There are numerous mobile applications available that make life easier and simpler.
With the advancement of technology, the risk also rises. Hackers come up with techniques to penetrate through and break into people’s data. It becomes essential for mobile app developers to become vigilant. They need to check, review, and update their applications in a way that is much more secure. They have to test, analyze, and investigate their application’s safety. For a developer to provide the best mobile application development services to its user, the most crucial element to be considered is Security.
‘’ As the world is increasingly interconnected, everyone shares the responsibility of Securing Cyberspace’’ – Newton Lee
Generally, the mobile app’s security is possible if there were flaws at the development stage of the app, or an application gets duplicated with additional functions that operate in the background and execute malicious activities. Here, the application gives in the sensitive data from the user’s device.
Mobile app developers should perform exhaustive security testing to check for flaws. Or even chances of penetration of data. Mobile app security testing helps to protect the applications from any external threats, malware, or other digital frauds. Especially, that put critical personal and financial information at risk to hackers.
For instance, Fortnite and PUBG mobile, the popular play on google, got cloned illegally multiple times. Hackers could gain the code base of the original app, create clones, and would steal the data of the device that would own the app.
 Google had to issue a warning on this issue to make sure users do not get app attacked. To assist in this area, a worldwide NGO, OWASP, Open Web Application Security Project, provides developers with guidelines to run their testing efficiently and create secure mobile apps.
Google had to issue a warning on this issue to make sure users do not get app attacked. To assist in this area, a worldwide NGO, OWASP, Open Web Application Security Project, provides developers with guidelines to run their testing efficiently and create secure mobile apps.
Threats to Mobile App Security
Mobile apps are a network for security threats. Hackers target the weak mobile app security systems and seek to profit from such app’s device users. Let’s see the risks that victim of digital frauds can face;
- Financial login credentials or details stolen
- Credit card details stolen and even resold
- Getting access to business networks
- Identity theft of user
- Spread of malware to uninfected devices
- Messages copied and scanned for private data
- Undesirable end-user experiences
- Negative impact on the brand’s reputation
- Ongoing financial crisis
Users are dependent and trust companies to test the mobile applications for security. That is, before making them available. But the developers fail to realize the impact of weak mobile application security. Thereby creating further victims of mobile app security scam.
For instance, in Sweden, in a financial hack, a new version of the banking hack could steal user credentials and credit card data from a user’s device. Its capacity to take control of the message feature of the device allowed it to manipulate and influence banking functions. Its code could manipulate twenty-four apps of different banks.
Preparation phase –To Create a Secure and Powerful Application
‘’True cybersecurity is preparing for what’s next, not what was last’’ – Neil Rerup.
Let’s look at the steps of creating a secure and powerful mobile app. The first step is Identification. Recognition of the data that is largely critical to the app or the device. To make sure the data is rightly identified, all the data that the application uses needs to be analyzed and check the risk level of that data. It will help evaluate the level of security that is required to safeguard the data.
In the next step, the developers’ design methods of protection to secure the data. Simply put, it means implementing the level of security to safeguard the data, decided in the earlier step. They take up embedding the security, keeping into consideration the client and server systems. And maintaining the commercial logic of the application. Here, all the security features are input into the concerned application.
The third and final step of the process is conducting a basic test to verify if all the implemented security and logic are a match. Once this gets accomplished, the app is ready to be assessed for quality and security excellence.
Being clear on the basic understanding of mobile app security and how developers can prepare themselves to enter the success phase of this safeguarding process, let’s look at a few ways to improve mobile app security.
Also Read: Why Should Start-ups Invest in Developing an Android App?
Measures to Improve Mobile App Security
An app can face many security threats. Like, data leakage, poor authentication of apps, irregular sessions, and failure of encryption. To put these issues to ease, there are measures developers can take to improve their mobile app security. Let’s have a look at them.
Security Planning
To ensure a good security system in place, start by planning how the security needs to be. Allocate the necessary resources to devising this plan. Consult, revise, and fixate on the most suitable plan of security for the mobile app.
Avoid Ignoring Updates
Many developers fail or do not pay heed to update their apps regularly. Which results in a lack of security against recently found vulnerabilities. Such updates tend to cover the latest security patches. And ignoring them exposes applications to the latest security threats.
API Verification
API, application programming interface, is the part of backend development. It helps apps to connect and form a network. Each application in a device must receive permission or API key to interact. But since their systems are external, they can be a security threat. For tightening the mobile app security, a strong API gateway can be installed.
Handling Sessions Effectively
Developers can handle user sessions more productively with the help of tokens. A token is a tiny hardware device used by a user to authorize access or a network service. Such tokens can be easily utilized, measured, or revoked.
Compelling High-level Authentication
Several security breaches are caused due to weak authentication. Authentication usually refers to setting up passwords. A developer needs to make sure the users employ safe passwords. And build powerful authentication. For instance, for your app, accept only strong alphanumeric passwords that need to be renewed in six months’ time.
Dual-factor authentication is another beneficial way to secure a mobile app. If an app allows dual-factor authentication, then in such a case, along with the password, the user needs to input a code sent via text or email to the user once the user tries to log in. With modern technology, advanced authentication methods involve biometrics like retina scans or fingerprints.
Understand Platform Limitations
While developing multiple mobile operating systems, it is ideal to know the security features, details, and limitations of the particular platform before inputting any code. Many factors need to be considered here, like encryption, user case scenarios, password support, or, location data. It would help to gain apt control and distribution of the app on said platform.
Encrypt with the Finest Tools and Techniques
For better encryption, make sure any user data gets stored safely. Storing the keys in secure containers is the best approach. Do not store locally on the device as it adds to the risk levels. Encrypted data containers or key chains, or even cookies for stored passwords can be exercised. Also, take into account the logs, which need to be deleted after a set interval of time, automatically, for best security.
Check Rooted Devices
Some devices or systems lets users root their device using third-party apps. However, not every user understands the exposure to manipulation from hackers or malware. Hence it becomes essential for developers to either not allow their app to be run in a rooted environment or else issue consistent warnings to the users about the same.
Frame Smart Access Policies
To lessen the risk of attack, make use of libraries or frameworks that are completely secure. The app needs to have policies that are easy, reliable, and align with general access policies followed.
Try RASP Security
Runtime application self-protection security system protects an app against attacks by providing visibility into hidden vulnerabilities. This software integrates with the app and continually intercepts calls made to the app from potential attackers.
The RASP layer scrutinizes the incoming traffic and also prevents fraudulent calls from affecting the app. All incoming requests get inspected by the RASP layer between the mobile application and the server.
Use Code Obfuscation
This technique simply means to protect an app from hackers by employing code obfuscation. It is to create a code that is extremely difficult for hackers to crack. Obfuscators help to automatically convert programming code into a format that cannot be understood by humans. It generally includes encrypting the code, removing metadata that reveals information about the libraries or the APIs, and renaming the variables so they cannot get predicted.
Test Everything
This measure points developers to test each and every step, plan, or procedure followed towards the app security. Each part is crucial and needs to get tested for quality security. Furthermore, developers should review the app regularly and work on security loopholes if any, that might result in data hacking. It is the key to create a secure and brilliant mobile app.
Conclusion
‘’Security is better when it’s built-in, not bolted on’’ – Stephen Yu
The mobile security app is the main responsibility of the developer. The impact of mobile app security goes beyond user experience and impacts the overall reputation of the brand. The growing hacking attempts and data breaches are making users opt only for a mobile app that provides security and safety.
So, for delivering the finest mobile application development services, developers need to work hard and grind to create applications that not only satisfy the user but also take care of the security facet.[/blog_single_full_content][/vc_column][/vc_row]